If you are visiting a website or reading an e-mail and there is some problem to read text due to color of page or the font too small. You can change the font and color as well to solve this problem.
- To increase or decrease your font size and color of webpage in Internet Explorer, select the Tools option from the top of your Explorer window and go to the Internet options.
- Here go the General option and then click on Accessibility button on right lower of the dialog box.
- Now change the status of checkbox marked "Ignore font sizes specified on Web pages" and next Ignore Colors specified on Web pages", end with Ok.
- For change the font size select to View option from the top menu and go to Text size option to change it.
10/17/07
How to Change the Font size of Web page?
เขียนโดย
kaeow
ที่
7:20 PM
0
ความคิดเห็น
![]()
How to Clean computer Casing ?
When you noticed your computer case is looking yellowish then you can understand about inner side of your computer case as dirty as outside. Because Dust is the main cause to heat up your system and heat link to hardware failure. You can save your computer maintenance cost if you clean your computer on the regular basis.
- Never place your computer on the ground, always use computer table or shelf for this purpose.
- To clean computer case first unplugs your system power from the electrical outlet. Remove all cables and connectors from the back side of your computer.
- Now use the compressed air and start clean from back to front of your computer case, specially casing and power supply fan.
- At the end using lightly dampened cloth or spray any cleaning fluids on the computer case and use paper towel to dry it.
- This process should be done after every three months if you want to save your system life.
เขียนโดย
kaeow
ที่
7:06 PM
0
ความคิดเห็น
![]()
10/11/07
How to speed up your Broadband internet connection?
You can increase the speed of your broadband internet connection, if you are using windows XP on your computer. This is built-in feature of windows XP to reserve the 20 percent of bandwidth of your internet connection, but you can override of this default setting. By enabling these setting, you can use this reserve bandwidth and enjoy your speedy broadband internet connection. You can set reserve able limit from 0 to 100 percent, but if you want to enjoy 100 percent bandwidth of internet connection, you should configure bandwidth limit 0 percent.
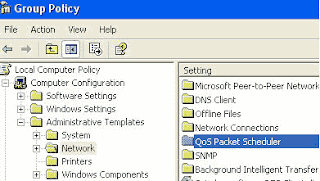
- First click on Start button then type "GPedit.msc" in Run option and press Enter.
- Under "Local Computer Policy" expand the "administrative templates".
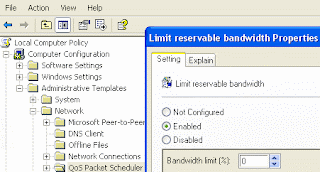
- Here in right side window expand the "Network" then highlight the "QoS Packet Scheduler".
- Now again in right side window, double click on "limit reservable bandwidth".
- Under the "Limit reservable bandwidth properties" dialog box check "enabled" then change the "Bandwidth limit % to zero.
- Now close the Group Policy editor and restart your compute, after any changes to go into effect.
เขียนโดย
kaeow
ที่
2:53 PM
0
ความคิดเห็น
![]()
10/8/07
How to Clear Your unnecessary backups files?
It is a good practice to make the backup of the important data. In many computer applications you can use the auto backup option to make the backup of a important file after specific time or set make auto backup on save. Normally backup files take up few kilobytes of your hard disk space but backup size depends upon the size of actual size.
But some time these auto backup files take up extra hard disk space and can slow your computer performance. You can clear these unnecessary backup files cluttering up you computer. First search and then delete these file. Search with some common backup file extensions, for example .bac, .bak, .bck, .bk!, .bk$. After search result you can delete the unnecessary backup files.
เขียนโดย
kaeow
ที่
1:43 PM
0
ความคิดเห็น
![]()
What to look for when you are buying a web cam.
IResolution: Standard rez is 320x240 but some will do 640x480. There is no resolution beyond VGA yet.
Frame rate: Aim for 30 frames per second. Most mid-priced cams will do this frame rate these days. Your internet connection will be the bottle neck on the frame rate.
Internet connection: You should also check the upload speed on you Internet connection. It is a fraction of the speed of your download connection. To get an image of 15 fps you need an upload speed of about 256 kbps.
Price: The higher the price the more onboard image processing in the camera. So if you have an old computer go up market on your webcam to take the load off the old PC.
Your PC's age: The older your PC the pricier the webcam you should buy because image processing will be done in the camera and not on the computer.
Lens: Typically it is not spelled out on the box but the pricier the cam the more likely it will have glass rather than a plastic lens. Glass will give you a clean image.
Light sensitivity:The higher end cams have better performance in low light.
Image: You'll get a sharper crisper image on the high end -- which is $79 to $99 US
Pan and tilt:Up at the top end of pricing you'll get pan and tilt capabilities. That's past the $100 US mark.
เขียนโดย
kaeow
ที่
1:35 PM
0
ความคิดเห็น
![]()
10/3/07
How to Enable the Windows Task Manager?
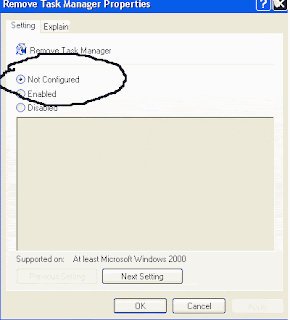
Windows Task Manager is used to view the status of running applications, active processes, CPU and Page file usage history and active user in windows environment. As a system administrator you can mange the all features of Windows Task Manager, you can end task any running application and set the priority of any running process according to application importance. By default Windows Task Manager Status is enabled, but a user can also disable or enable it manually. But some time a registry hack applies on windows task manager to disable it and your system give you a message” Task Manager has been disabled by your administrator.” then you should enable it with editing the system registry or using Group Policy Editor. To enable this feature, you will need to be logged into your computer with administrative rights. Now click on Start button and type “Gpedit.msc” in Run option then press OK.
Before proceeding further, first scan your system with up-to-date antivirus, and then follow the given steps to enable it using group policy editor.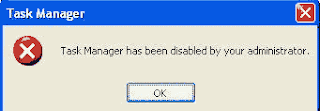
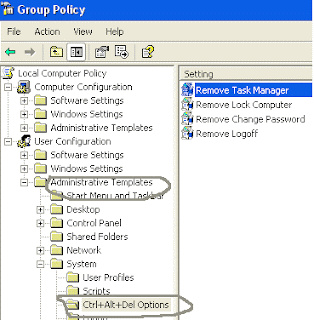
-
In Group Policy Editor, expand the “Administrative Templates” > “System” then “Ctrl+Alt+Del Options”, under the User Configuration option.
-
Now in right side of panel “Ctrl+Alt+Del Options” double click on “Remove Task Manager” to change it setting. Here set the option “Disable” to “Enable” or “Not configured” and your task manager is available once again.
เขียนโดย
kaeow
ที่
7:05 PM
0
ความคิดเห็น
![]()
9/30/07
What is Bluetooth Technology?
Bluetooth is a wireless technology that enables any electrical device to wirelessly communicate in the range of 2.5 GHz ISM frequency band. Mobile phones, headsets, PDA's and portable computers can communicate and send data to each other without wires or cables to link to devices together. The name of Bluetooth derived from the name of an English king Harold Bluetooth.
It a low cost, low power, radio technology, which is particularly suited to the short range Personal Area Network (PAN) application. Bluetooth Special Interest Group is authorized to develop its specifications & license.
The Main Features of Bluetooth are given below:
- It operates in the 2.4GHz frequency band without having a license for wireless communication.
- Up to 10-100 meters data can be transfer in real time.
- Close proximity & accuracy is not required for Bluetooth as in case of infrared data (IrDA) communication device. Bluetooth does not suffer from interference from obstacles such as walls while infrared suffers due to obstacles.
- Bluetooth supports both point-to-point and point-to-multipoint wireless connections without cables between mobile phones and personal computers.
- Data transfer rate of blue tooth varies from version to version. Data rate of 1 Mbps for Version 1.2 Up to 3 Mbps for Version 2.0.
Then major parts of Bluetooth system are RF transceiver, base band, and protocol stack. Bluetooth is used for small-area networking without user intervention. Due to extremely low transmission power in Bluetooth technique battery power is saved. It is a networking standard that works at two levels:
· Physical level.
· Protocol level
Due to these levels mobiles have to agree on these levels when bits are sent. It decides the amount of data to be sent at a time, and how the parties in a conversation can be sure that the message received is the same as the message sent.
Bluetooth networking transmits data through low-power radio waves. It can connect up to eight devices simultaneously. With in the range of about ten meters you must think that the devices will not interfere with each other. Bluetooth solved the problem of devices interference while sending the data by using the technique of Spread-Spectrum Frequency Hopping due to which devices may transfer data at the same frequency at the same time. The question rises here is how Bluetooth send the same data using same frequency band without devices interferences? In Bluetooth technique, transmitters change frequencies 1,600 times in every second. In this way devices can make full use of a limited band of the radio spectrum.
When Bluetooth devices came into the range of each other, conversations take place automatically. This conversation automatically determines whether they have the data to share or not. In this way Bluetooth devices not only share the data but also control the data to be transferred. When the connection is established, the devices either they are part of a computer system or a network, Bluetooth systems create a personal-area network.
The technology used in Bluetooth also provides security in three ways:
· Pseudo-random frequency hopping,
· Authentication,
· Encryption.
Frequency hops make it difficult for anyone to eavesdrop. Authentication allows a user to limit connectivity to specified devices. Encryption uses secret keys to make data intelligible only to authorized parties.
Service-level security and device-level security work together to protect Bluetooth devices from unauthorized data transmission.
Many serious problems create only due to improper security issues. Some of them are given below:
- Blue jacking
- Blue bugging
- Car Whisperer
Blue Jacking
It is used to send a business card in the form of text message via Bluetooth to other users. It should be noted that the distance between two users is not more than 10 meters. If the user doesn't found the proper text, he should add the contact to his phone book. After saving his contact in his address book retry to send the same message. In this way the user can get business card from other user via Bluetooth. It’s all because of the known destination from where the massage is being coming.
Blue Bugging
Due to this hackers can access user’s phone. It not only access one’s mobile phone, but also use its features including placing call, messaging. Even though the user doesn't realize it’s happening.
Car Whisperer
Car whisper is a type of software due to which hackers can send and receive audio file from a Bluetooth-enabled car stereo.By.." http://www.computerfreetips.com/"
เขียนโดย
kaeow
ที่
7:18 AM
0
ความคิดเห็น
![]()
Hangs up internet dial-up connection
- To disable the call waiting option, first click on Start button, then Network Connections.
- Here double click on your internet connection and click on Properties button then General.
- Under General tab select Use Dialing Rules box then click on dialing rules button.
- Here select My Location then click on Edit button. Under General tab select the option To disable call waiting dial and put any number in next box like.
- At the end click on Ok button and dial your connection again.
Thank you "http://www.computerfreetips.com" for detail.
Set Explorer Multiple Homepages
Follow the given steps to set multiple home pages in Internet Explorer.
- First open the Internet Explorer 7 and go to the option Tools then click on Internet Options.
- Select the General tab, here you will get option "To create home page tabs, type each address on its own line" and type the URL in the Home page section.
- Type one URL in one line then press Enter to type another URL. Press Ok to finish.
Thank you "http://www.computerfreetips.com" for detail.
How to Outlook Express Back up?
Outlook Express data is usually stored at the following paths be defaults but you can change Outlook Express location. Normally Outlook Express folder location is C:\ drive when you install your window on C drive, but you can change location of you Outlook to other drive, Outlook Express e-mail message store, along with the address book, usually resides in subfolders at the following paths:
C:\Documents and Settings\User Name\Application Data\Identities\
C:\Documents and Settings\User Name\Application Data\Microsoft\Outlook Express\
C:\Documents and Settings\All Users\Application Data\Microsoft\Outlook Express\
C:\Documents and Settings\User Name\Application Data\Microsoft\Address Book\




![Validate my Atom 1.0 feed [Valid Atom 1.0]](valid-atom.png)